How To Turn On Active Directory Windows 7
First published on MSDN on Apr 10, 2017
Step-past-stride guide for setting up LDAPS (LDAP over SSL)
The guide is split into 3 sections :
- Create a Windows Server VM in Azure
- Setup LDAP using Advertising LDS (Active Directory Lightweight Directory Services)
- Setup LDAPS (LDAP over SSL)
NOTE : The following steps are similar for Windows Server 2008, 2012, 2012 R2 , 2016. In this article, we will utilise Windows Server 2012 R2.
Create a Windows Server VM in Azure
Create a VM named "ldapstest" Windows Server 2012 R2 Datacenter Standard DS12 using the instructions here: Create a Windows virtual machine with the Azure portal
Connect to the VM ldapstest using Remote Desktop Connection.
Setup LDAP using AD LDS
Now let us add AD LDS in our VM ldapstest
Click on Start --> Server Manager --> Add together Roles and Features. Click Next.
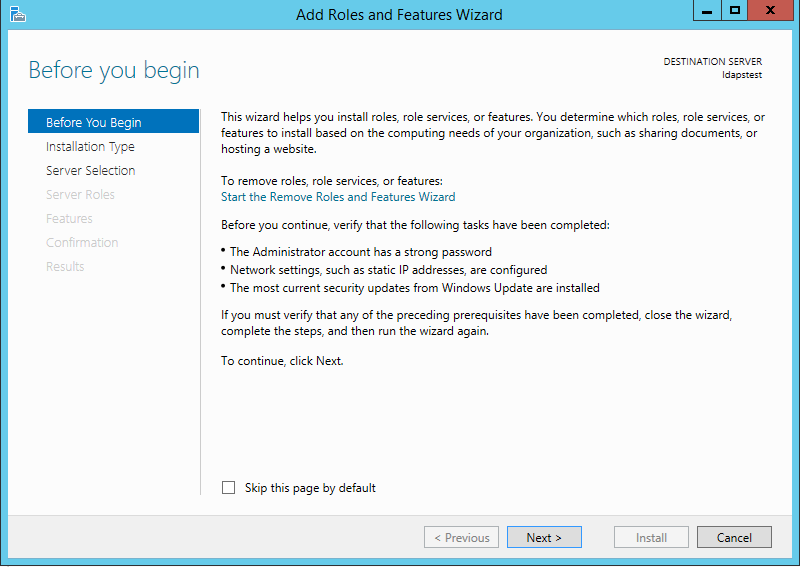
Choose Role-based or feature-based installation. Click Next.
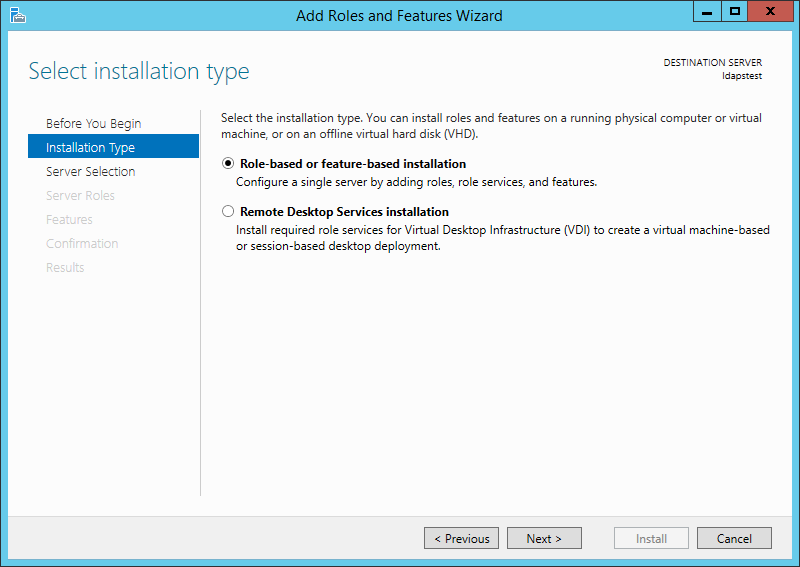
Select ldapstest server from the server pool. Click Next.
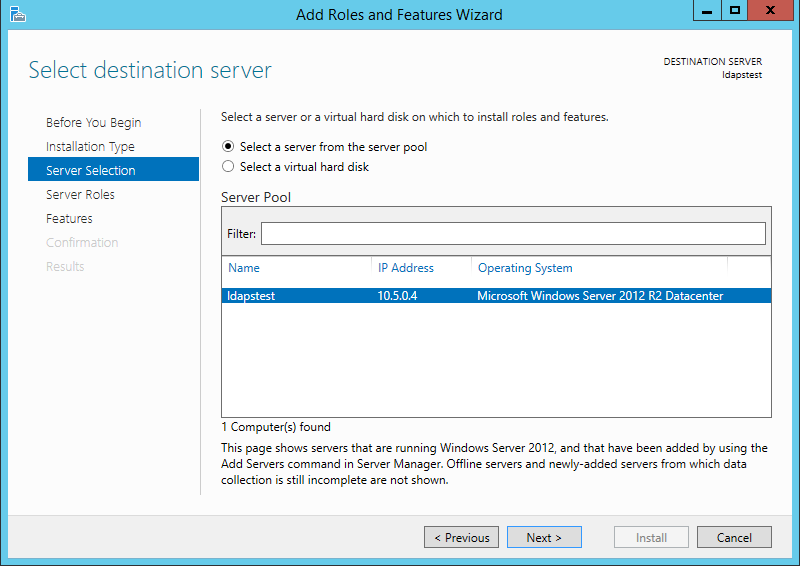
Mark Active Directory Lightweight Directory Services from the list of roles and click Next.
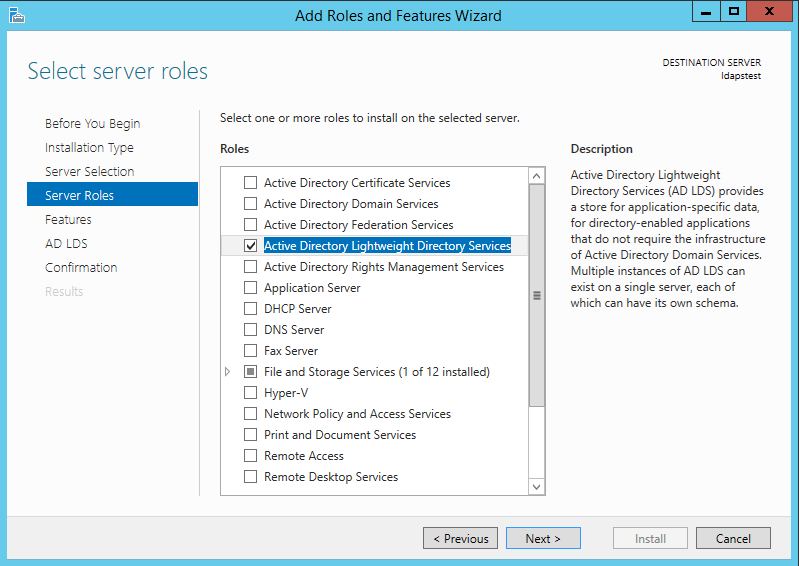
From the list of features, choose zip – just click Side by side.
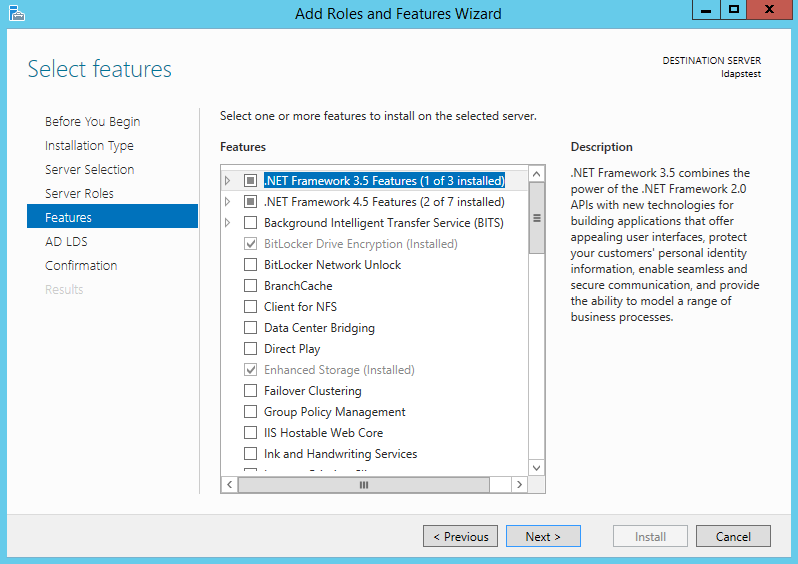
Click Side by side.

Click Install to first installation.

One time installation is complete, click Close.

At present nosotros accept successfully set up AD LDS Role. Let usa create a new Advertizing LDS Instance "CONTOSO" using the magician. Click the "Run the Agile Directory Lightweight Directory Services Setup Wizard" in the above screen. And and so Click Shut.

Choose Unique Instance since we are setting it up for the start time.

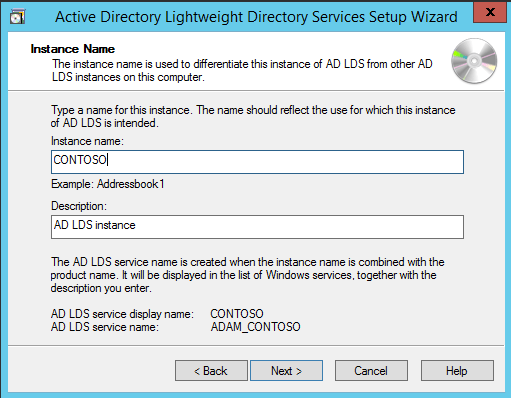
Type "CONTOSO" in Instance Name and click Next.
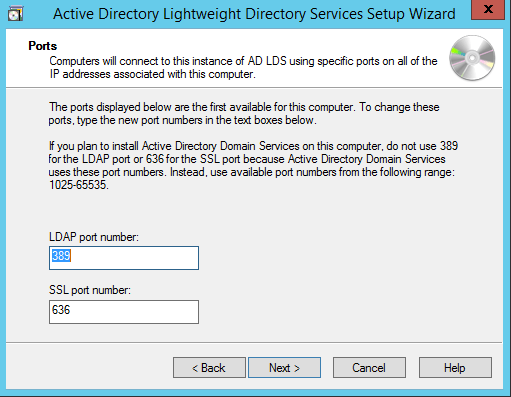
By Default, LDAP Port is 389 and LDAPS port is 636, allow united states of america choose the default values - click Adjacent.
Create a new Application Directory Partitioning named "CN=MRS,DC=CONTOSO,DC=COM". Click Next.

Using the default values for storage location of ADLDS files- Click Next.

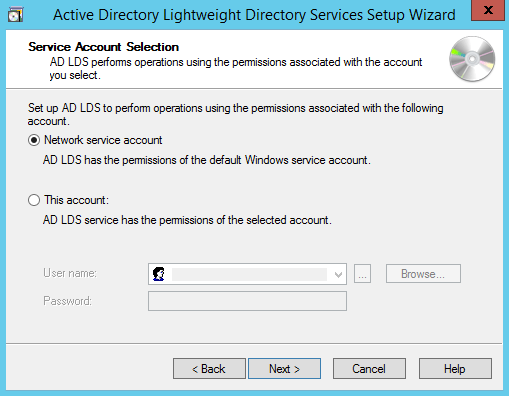
Choosing Network Service Business relationship for running the Advertizement LDS Service.
You will receive a prompt warning about information replication. Since we are using a single LDAP Server, nosotros can click Yes.

Choosing the currently logged on user every bit an administrator for the Ad LDS Example. Click Next.

Mark all the required LDIF files to import (Here nosotros are marking all files). Click Side by side.

Verify that all the selections are right then Click Next to confirm Installation.
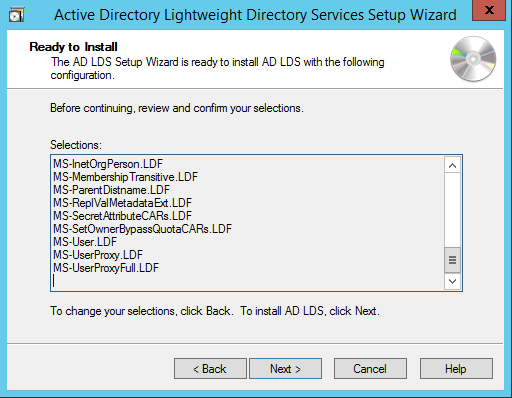
Once the instance is setup successfully, click Finish.

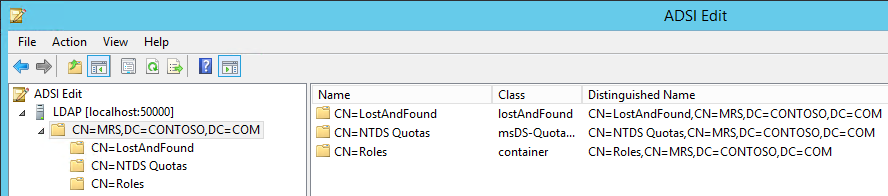
Now let u.s. attempt to connect to the Advertisement LDS Example CONTOSO using ADSI Edit.
Click on Start --> Search "ADSI Edit" and open information technology.
Correct Click on ADSI Edit Binder (on the left pane) and choose Connect To.. . Fill the following values and Click OK.
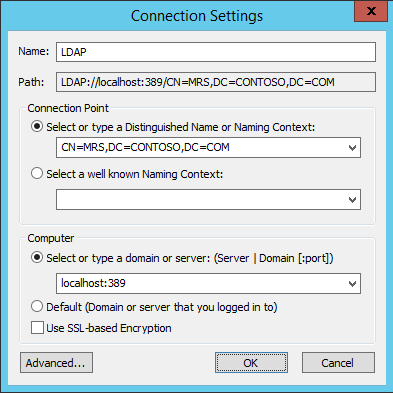
If the connectedness is successful, we will be able to browse the Directory CN=MRS,DC=CONTOSO,DC=COM :
Setup LDAPS (LDAP over SSL)
The Document to be used for LDAPS must satisfy the following 3 requirements:
• Certificate must be valid for the purpose of Server Authentication. This means that it must also contains the Server Authentication object identifier (OID): 1.three.half dozen.1.5.5.7.3.1
• The Subject name or the first name in the Subject Culling Proper name (SAN) must match the Fully Qualified Domain Proper noun (FQDN) of the host car, such as Subject:CN=contosoldaps. For more information, run across How to add together a Subject Alternative Name to a secure LDAP document .
• The host machine account must have access to the individual fundamental.
Now, allow'south use Agile Directory Certificate Services to create a certificate to be used for LDAPS. If you already have a certificate satisfying the in a higher place requirements, you lot can skip this footstep.
Click on Outset --> Server Manager --> Add Roles and Features. Click Side by side.
Choose Role-based or characteristic-based installation. Click Next.

Select ldapstest server from the server pool. Click Side by side.

Choose Active Directory Certificate Services from the list of roles and click Next.

Choose nothing from the list of features and click Side by side.
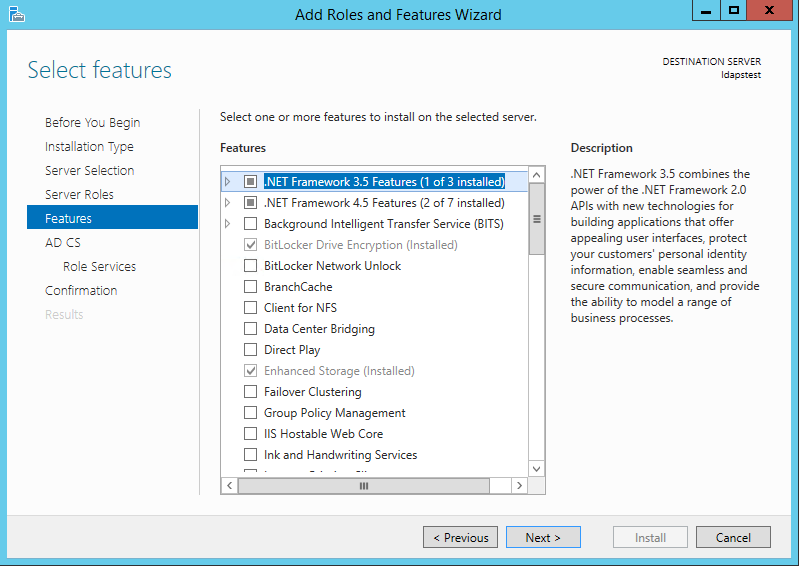
Click Side by side.

Marking "Certificate Dominance" from the list of roles and click Next.
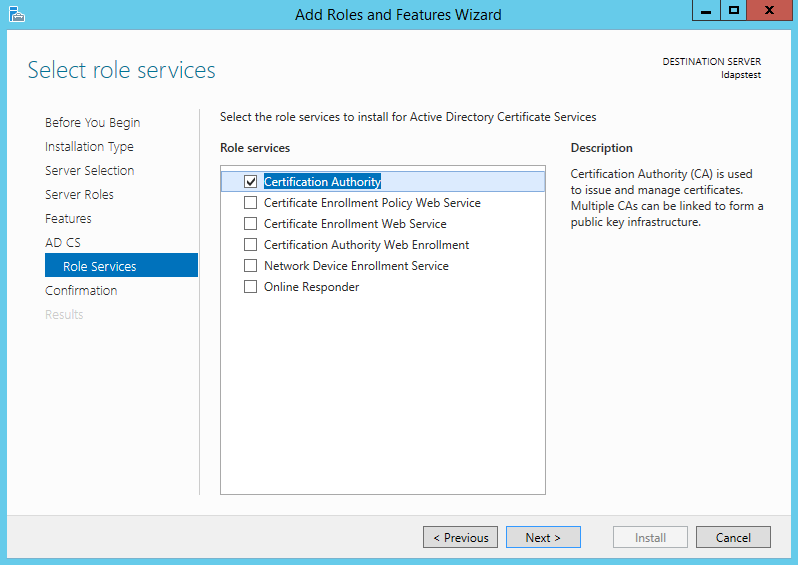
Click Install to confirm installation.

Once installation is complete, Click Close.

Now let's create a certificate using Advertizement CS Configuration Sorcerer. To open the wizard, click on "Configure Agile Directory Certificate Services on the destination server" in the in a higher place screen. And and so click Close. We can utilise the currently logged on user azureuser to configure office services since information technology belongs to the local Administrators group. Click Side by side.
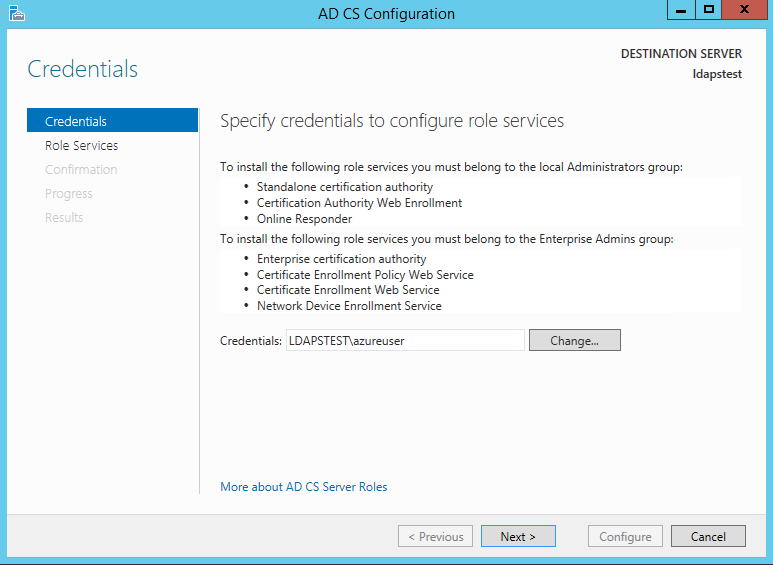
Choose Certification Say-so from the list of roles. Click Next.

Since this is a local box setup without a domain, we are going to choose a Standalone CA. Click Next.

Choosing Root CA as the type of CA, click Adjacent.
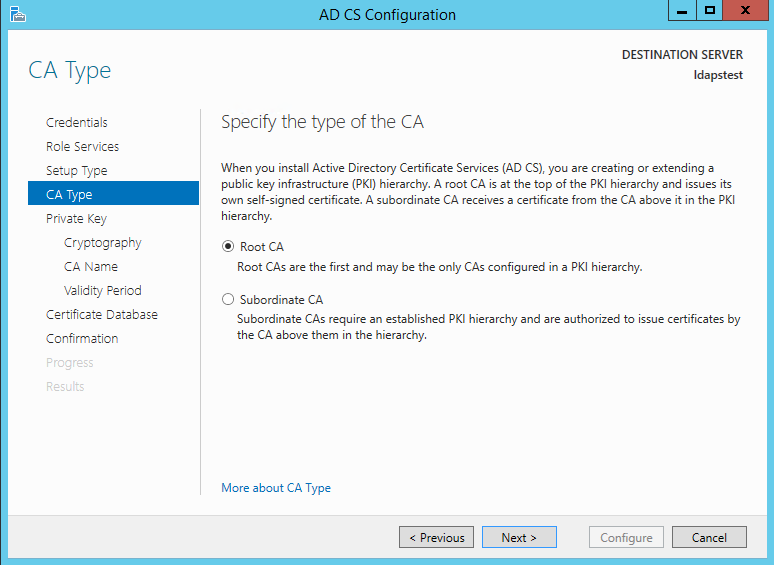
Since we do not possess a individual key – let'southward create a new 1. Click Next.

Choosing SHA1 as the Hash algorithm. Click Next.
UPDATE : Recommended to select the nearly contempo hashing algorithm since SHA-1 deprecation countdown
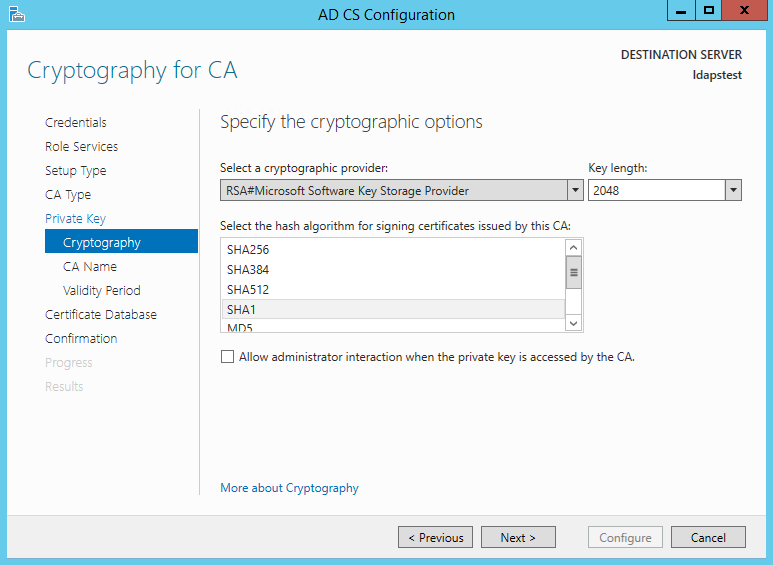
The name of the CA must match the Hostname (requirement number 2). Enter "LDAPSTEST" and Click Next.

Specifying validity menses of the document. Choosing Default 5 years. Click Next.

Choosing default database locations, click Adjacent.

Click Configure to confirm.
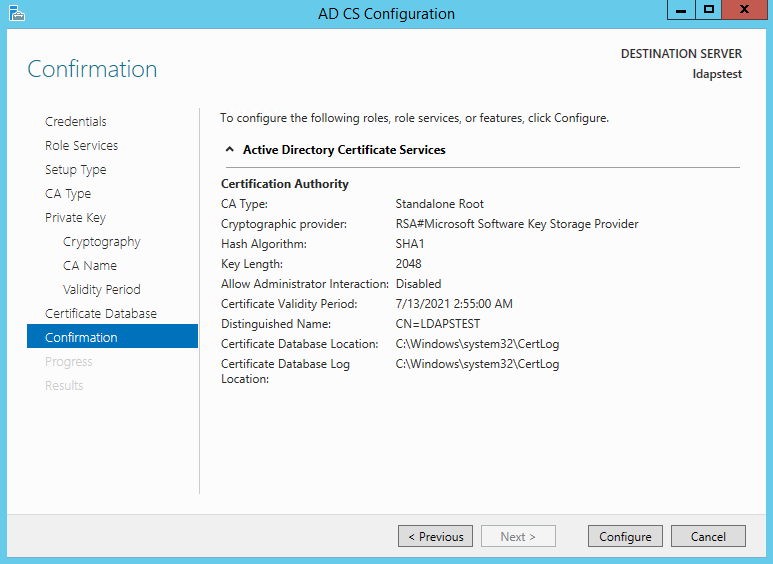
Once the configuration is successful/complete. Click Close.

Now let the states view the generated certificate.
Click on Start à Search "Manage Reckoner Certificates" and open it.
Click on Personal Certificates and verify that the certificate "LDAPSTEST" is present:
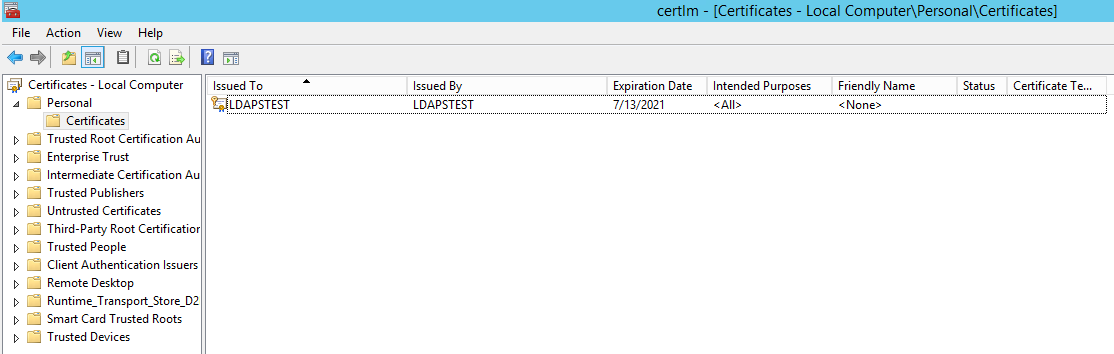
Now to fulfill the third requirement, let us ensure host auto account has admission to the private fundamental. Using the Certutil utility, find the Unique Container Name. Open up Command Prompt in Ambassador mode and run the following command: certutil -verifystore MY

The private key will be nowadays in the following location C:\ProgramData\Microsoft\Crypto\Keys\<UniqueContainerName>
Right Click C:\ProgramData\Microsoft\Crypto\Keys\874cb49a696726e9f435c1888b69f317_d3e61130-4cd8-4288-a344-7784647ff8c4 and click backdrop --> Security and add together read permissions for NETWORK SERVICE.

We need to import this certificate into JRE key shop since our certificate "CN=LDAPSTEST" is non signed past whatsoever past any trusted Certification Potency(CA) which is configured in y'all JRE keystore due east.g Verisign, Thwate, goDaddy or entrust etc. In order to import this certificate using the keytool utility, permit us starting time export this cert as a .CER from the car certificate store:
Click Start --> Search "Manage Computer Certificates" and open it. Open personal, right click LDAPSTEST cert and click "Export".

This opens the Document Export Sorcerer. Click Next.

Do not consign the private key. Click Next.

Choose Base-64 encoded X .509 file format. Click Adjacent.

Exporting the .CER to Desktop. Click Adjacent.

Click Finish to complete the document export.

Certificate is now successfully exported to "C:\Users\azureuser\Desktop\ldapstest.cer".
Now nosotros shall import it to JRE Keystore using the keytool command present in this location:
C:\Program Files\Java\jre1.eight.0_92\bin\keytool.exe.
Open up Control Prompt in administrator manner. Navigate to "C:\Program Files\Coffee\jre1.8.0_92\bin\" and run the following command:
keytool -importcert -alias "ldapstest" -keystore "C:\Programme Files\Coffee\jre1.eight.0_92\lib\security\cacerts" -storepass changeit -file "C:\Users\azureuser\Desktop\ldapstest.cer"

Blazon "yeah" in the Trust this document prompt.
Once document is successfully added to the JRE keystore, nosotros can connect to the LDAP server over SSL.
Now allow united states of america endeavour to connect to LDAP Server (with and without SSL) using the ldp.exe tool.
Connection strings for
LDAP:\\ldapstest:389
LDAPS:\\ldapstest:636
Click on Outset --> Search ldp.exe --> Connection and fill in the following parameters and click OK to connect:
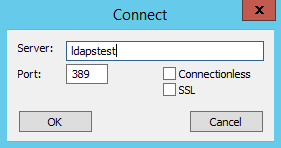
If Connexion is successful, you lot will run across the following message in the ldp.exe tool:

To Connect to LDAPS (LDAP over SSL), utilize port 636 and marker SSL. Click OK to connect.

If connection is successful, you volition see the following message in the ldp.exe tool:

REFERENCES
https://technet.microsoft.com/en-u.s.a./library/cc770639(v=ws.10)
https://technet.microsoft.com/en-usa/library/cc725767(v=ws.10).aspx
http://social.technet.microsoft.com/wiki/contents/articles/2980.ldap-over-ssl-ldaps-certificate....
https://blogs.technet.microsoft.com/askds/2008/03/13/troubleshooting-ldap-over-ssl/
http://javarevisited.blogspot.com/2011/11/ldap-hallmark-active-directory.html
Source: https://techcommunity.microsoft.com/t5/sql-server-blog/step-by-step-guide-to-setup-ldaps-on-windows-server/ba-p/385362
Posted by: walstonlond1985.blogspot.com

0 Response to "How To Turn On Active Directory Windows 7"
Post a Comment